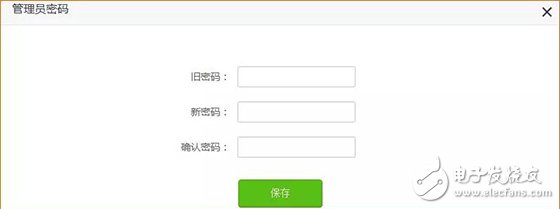
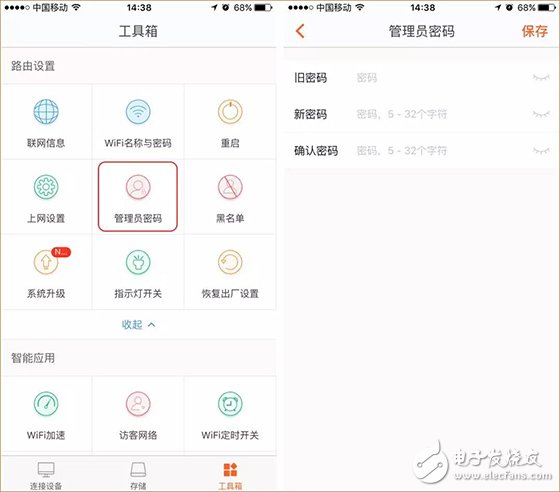
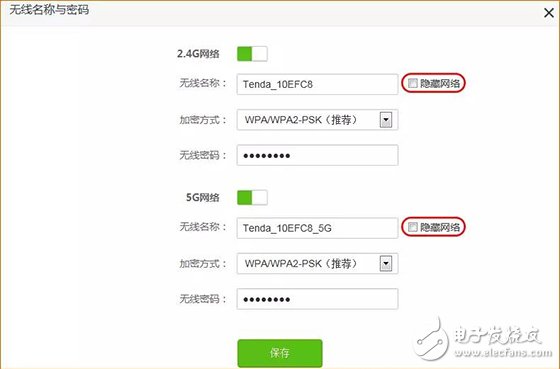
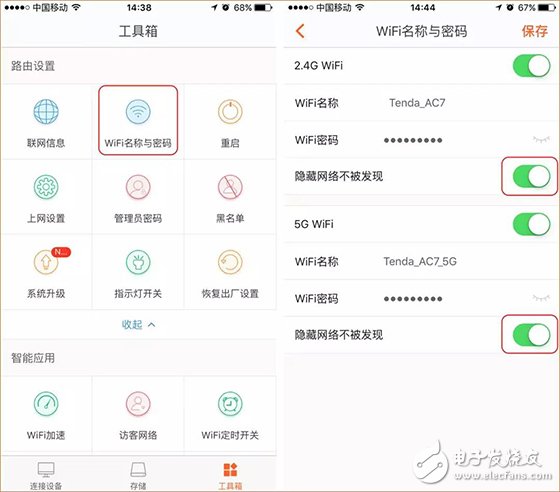
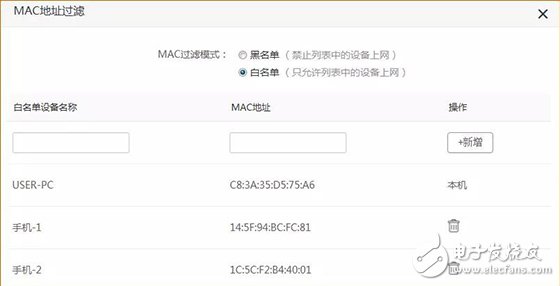
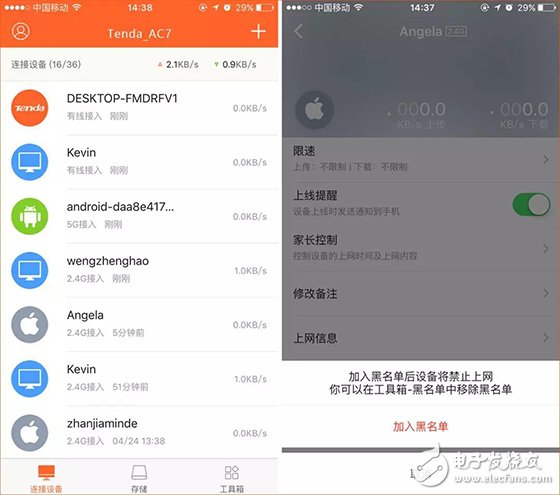
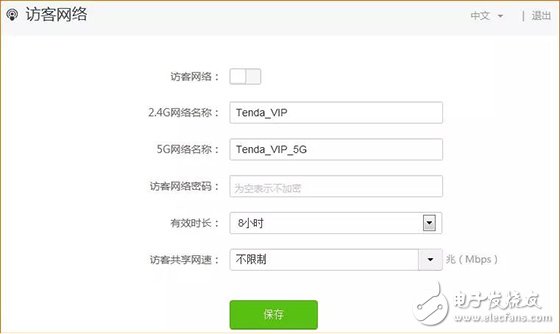
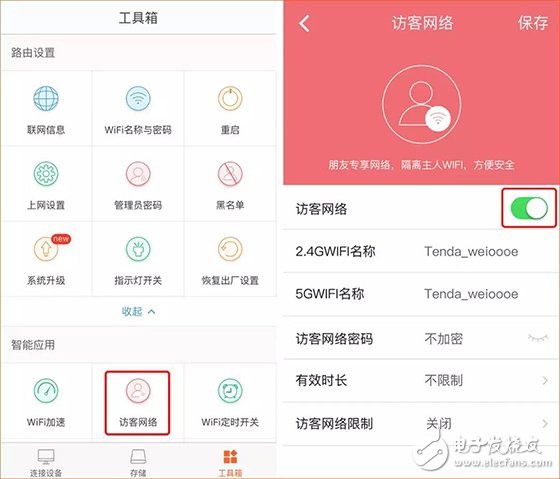
Last week, CCTV’s "Economic Half-hour" column broadcasted "The Master Key to Stealing Passwords", and made in-depth reports on the "WiFi Master Key" and "WiFi Key" two web applications, from individuals to Shopping malls, from the diplomatic building to the financial building, can easily steal passwords and connect smoothly, and even access some WiFi back-end data information. Many state agencies, financial institutions and 900 million users are like “streakingâ€. è¹ç½‘APP will snoop and steal all kinds of WiFi information from the surrounding and passing locations through the user's mobile phone. In addition, this kind of software not only steals WiFi passwords, but also can view personal privacy information such as WeChat. The whole process is without the user's knowledge. Completed. The operation principle of WiFi network software is to share passwords without cracking passwords. After installing this software, the WiFi password stored in your mobile phone will be uploaded to the background of the software and then shared for use by nearby people. What's even more disgusting is that even if you don't have this app, but you happen to be a relative, he has this kind of network software, connected to your home's WiFi, your home's WiFi password will be shared. Even more frightening is that some apps will ask for your name, date of birth, ID number, address, phone number, account number and password, time, location, bank card and mobile phone address book. After being investigated by CCTV and the Ministry of Industry and Information Technology, the WiFi Master Key responded by saying: We have always attached importance to the protection of passwords, using 128-bit asymmetric encryption for passwords, and never displaying passwords in plain text. In addition, if the user or hotspot owner encounters property damage due to the use of the WiFi master key, the claim can be made. Although the APP indicates that the password is not displayed in plain text, and the property can be claimed for damages, who can guarantee that the property damage will be recovered? Can we only wait for the "è¹"? Is there any trick to prevent smashing nets? That must be there! Anti-mite network skills, the following takes the interface of Tenda AC7 as an example: Set the router administrator password Management password is the most important barrier in the background of the router. Do not set a password or use the original password, such as: admin, 123456, etc., please be sure to set the password carefully to prevent the network from entering the router and manipulating the home network. Setting method: 1. Enter the router setting interface 192.168.0.1, click "System Management" - "Administrator Password" to modify; 2. Set up via mobile app, download “Tenda WiFi†management app, open the app, click “toolbox†- “admin password†to modify. Hide the WiFi Hidden WiFi by turning off WiFi's SSID broadcast, so strangers can't search for your home's WiFi signal, reducing the chance of WiFi being smashed. = Setting method: 1. Enter the router setting interface 192.168.0.1, click "Wireless Settings" - "Wireless Name and Password" - check "Hide Network" - click "Save" to hide WiFi. 2. Open the “Tenda WiFi†management app, click on “Toolbox†– “WiFi Name and Password†– enable “Hide Network Not Found†– click “Save†to hide WiFi. Bind MAC address With MAC address filtering, you can add MAC address filtering rules and set the permissions for the specified MAC address to access the Internet, including "Allow access to the Internet" (whitelist), "Prohibit access to the Internet" (blacklist). Generally, we use the "white list" mode. After the setting is completed, unless it is a device that has already been added, other unfamiliar devices cannot connect to the Internet even if they successfully know the WiFi password. One button pull black Tenda supports APP management routers are equipped with the "one-click blacklist" function. When a strange device is connected to the home WiFi, the "Tenda WiFi" management APP can be used to pull a black button. After pulling the black, the black The device can no longer be smashed. Guest network If a friend comes to the house and needs to connect to the WiFi, you can open the guest network for friends. The guest network is isolated from the main network. Therefore, even if the friend's mobile phone has a web-based APP, it is not afraid to reveal the WiFi password of the owner's network. Setting method: 1. Enter the router setting interface 192.168.0.1, click "Guest Network" - enable this function and set the relevant wireless signal name, wireless password, effective Internet time, network speed sharing, and then click "Save"; 2. Open the “Tenda WiFi†management app, click “Toolbox†– “Guest Network†– enable this function and set the relevant wireless signal name, wireless password, effective Internet time, network speed sharing, and then click “Saveâ€.
The 8-inch tablet will have a big impact on the 7-inch and 10-inch tablet market. Because the portability of an 8-inch tablet is stronger than that of a 10-inch tablet, and the usable area is larger than that of a 7-inch tablet. The most important thing is that the price is more moderate, which is much cheaper than a 10-inch tablet. It can be said that the 8-inch tablet computer has a good balance between portability and screen display area, and is more likely to be favored by the majority of users.
8 Inches Tablet Pc,Tablet Computer,8 Inch Android Tablets,8 Inch Tablet Jingjiang Gisen Technology Co.,Ltd , https://www.jsgisentec.com