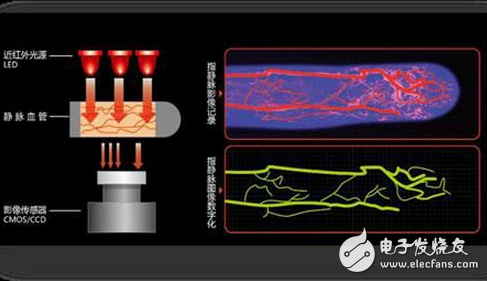
Biometrics is currently the most convenient and safe identification technology. The use of biometrics for identification is safe, reliable and accurate. In addition, biometric technology products are all realized with the help of modern computer technology, which is easy to integrate with computers, the Internet, and security, monitoring, and management systems to achieve automated and intelligent management. Therefore, biometric authentication technology has greater advantages than traditional authentication technology. The so-called biometric technology is the close integration of computers with high-tech methods such as optics, acoustics, biosensors and biostatistics, and the use of inherent physiological characteristics of the human body (such as fingerprints, facial features, iris, etc.) and behavioral characteristics (such as handwriting) , Voice, gait, etc.) for personal identification. Biometrics is an identification technology that relies on the physical characteristics of the human body for identity verification. It is widely used in access control, time and attendance, finance, public security and terminal electronic equipment because of its characteristics of no loss, no forgetting, uniqueness, immutability, good anti-counterfeiting performance and convenient use. Below we will talk about the five major biometric technologies commonly used in smart door locks Each fingerprint has several unique and measurable feature points, and each feature point has about seven features. People’s ten fingers produce at least 4,900 independently measurable features. Fingerprint recognition technology analyzes the measurable characteristic points of fingerprints, extracts characteristic values ​​from them, and then performs authentication. Verify its true identity. Every person (including fingerprints) has different skin patterns in patterns, break points and intersections, that is to say, they are unique and remain the same for life. Relying on this uniqueness and stability, we can create fingerprint recognition technology. This is the mainstay of the biometrics camp, and it is currently the most widely used biotechnology due to its low cost. advantage Fingerprints are unique features of the human body, and their complexity is sufficient to provide sufficient features for identification. If you want to increase reliability, you only need to register more fingerprints and identify more fingers, up to ten, and each fingerprint is unique. Scanning fingerprints is fast and very convenient to use. When reading fingerprints, users must touch their fingers with the fingerprint collector. Direct contact with the fingerprint collector is the most reliable way to read human biometrics. This is also one of the main reasons that fingerprint recognition technology can occupy most of the market. The fingerprint collection head can be more miniaturized, and the price will be lower. Disadvantage The fingerprints of some people or groups of people are difficult to image because of the few fingerprint features. In the past, the use of fingerprints in criminal records made some people afraid of "recording fingerprints." However, in fact, the current fingerprint authentication technology can guarantee that it does not store any data containing fingerprint images, but only stores the encrypted fingerprint characteristic data obtained from the fingerprint. Every time a fingerprint is used, the user's fingerprint print will be left on the fingerprint collecting head, and these fingerprint traces may be used to copy the fingerprint. Some products (such as smart locks equipped with optical fingerprint readers) are threatened by fingerprint replication. Different skins, skin humidity conditions, and fingerprint recognition authentication effects are also very different. Therefore, smart locks have a lot of room for improvement in terms of adaptability, rejection rate, and false recognition rate. Face recognition is a kind of biometric recognition technology based on human facial feature information. Use a camera or camera to collect images or video streams containing human faces, and automatically detect and track human faces in the images, and then perform a series of related technologies on the detected human faces, usually also called face recognition and facial recognition. The human face is innate like other biological characteristics of the human body (fingerprints, iris, etc.). Its uniqueness and good characteristics that are not easy to be copied provide the necessary prerequisites for identity authentication. Advantage Easy to use, user-acceptable face recognition technology uses a general-purpose camera as an identification information acquisition device to complete the identification process in a non-contact manner without the identification object being noticed. Intuitiveness highlights the use of facial recognition technology based on human facial images, and human faces are undoubtedly the most intuitive information source that can be distinguished by the naked eye, which is convenient for manual confirmation and auditing, and "judging people by their appearance" conforms to the law of human cognition. The recognition accuracy is high and the speed is fast. Compared with other biological recognition technologies, the recognition accuracy of face recognition technology is at a higher level, and the false recognition rate and rejection rate are lower. Not easy to counterfeit In applications with high security requirements, face recognition technology requires that the recognition object must be at the recognition site in person, and it is difficult for others to counterfeit. The unique active discrimination ability of face recognition technology ensures that others cannot deceive the recognition system with inactive photos, puppets, and wax figures. This is difficult to achieve with biometric technology such as fingerprints. For example, using the severed finger of a legitimate user can impersonate the identity of a legitimate user and make the identification system undetectable. General-purpose equipment The equipment used in face recognition technology is general PCs, cameras and other conventional equipment. Since computers and closed-circuit television monitoring systems have been widely used, there is no need for most users to use face recognition technology. A large number of special equipment, which not only protects the user's original investment, but also expands the functions of the user's existing equipment, and meets the user's security requirements. Basic information is easy to obtain, and the basis of face recognition technology is face photos or face images taken in real time, so it is undoubtedly the easiest to obtain. Low cost and easy to popularize. Because the face recognition technology uses conventional general-purpose equipment, the price is within the acceptable range of general users. Compared with other biometric technology, face recognition products have a high performance price. ratio. In a nutshell, face recognition technology is a high-precision, easy-to-use, high-stability, difficult-to-fake, and cost-effective biometric recognition technology, which has extremely broad market application prospects. Disadvantage Facial recognition is considered to be one of the most difficult research topics in the field of biometrics and even in the field of artificial intelligence. The difficulty of facial recognition is mainly caused by the characteristics of the face as a biological feature. There is little difference between individuals with different similarities, all facial structures are similar, and even the structural appearance of facial organs are very similar. Such a feature is advantageous for using faces for positioning, but it is disadvantageous for using faces to distinguish human individuals. The appearance of a variable face is very unstable. People can produce many expressions through changes in the face, and the visual images of the face are also very different at different viewing angles. In addition, facial recognition is also affected by light conditions (such as day and night, indoors). And outdoor, etc.), many face coverings (such as masks, sunglasses, hair, beards, etc.), age and other factors. In facial recognition, the first type of changes should be amplified and used as a criterion for distinguishing individuals, while the second type of changes should be eliminated because they can represent the same individual. Usually the first type of change is called the inter-class change, and the second type of change is called the intra-class change. For faces, intra-class changes are often greater than inter-class changes, which makes it extremely difficult to distinguish individuals by using intra-class changes under the interference of intra-class changes. Every iris contains a unique structure based on features like crowns, crystals, filaments, spots, pits, wrinkles and stripes. Iris recognition technology uses the characteristics of lifelong invariance and difference of iris to identify identity. Moreover, after the iris is formed in the developmental stage of the fetus, it will remain unchanged throughout the life course. These characteristics determine the uniqueness of iris characteristics, and also determine the uniqueness of identification. Therefore, the iris feature of the eye can be used as the identification object of each person. Iris measurement technology can read 266 feature points, while other biometric technologies can only read 13-60 feature points. According to data from Fujitsu, the false recognition rate of iris recognition is 1/1.500000, which is higher than 1/50,000 of fingerprint recognition, and is more suitable as a "password". The iris recognition is a non-contact recognition, which is very convenient and efficient. advantage It is fast and convenient, and you do not need to carry any documents to achieve door control, which can be one-way or two-way; it can be authorized to control one door or control to open multiple doors; Flexible authorization, according to the needs of management, user rights can be adjusted arbitrarily, and user dynamics can be understood at any time, including customer identity, operating location, function and time sequence, etc., to achieve real-time intelligent management; Unable to copy, the iris information is a password and cannot be copied; and every activity can be automatically recorded, which is convenient for traceability and inquiries, and an automatic alarm will be triggered for illegal situations; The configuration is flexible and diverse. Users and managers can set different installation and operation methods according to their own preferences, needs or occasions. For example, in public places such as lobby, you can only use the password input method, but in important occasions, the password is prohibited, and only the iris recognition method is used. Of course, the two methods can also be used at the same time; With low investment and maintenance-free, the assembly system can retain the original lock, but its mechanical moving parts are reduced, and the movement range is small, and the life of the door bolt is longer; the system is maintenance-free, and can be expanded and upgraded at any time without repurchasing equipment. In the long run, the benefits are significant and the management level can be greatly improved. Disadvantage It is difficult to miniaturize the size of image acquisition equipment; The equipment cost is high and cannot be widely promoted; The lens may produce image distortion and reduce reliability; Two modules: hardware and software; An automatic iris recognition system consists of two modules: hardware and software: iris image acquisition device and iris recognition algorithm. They correspond to the two basic problems of image acquisition and pattern matching respectively. The production of human language is a complex physiological and physical process between the human body’s language center and the vocal organs. The vocal organs that people use when speaking-tongue, teeth, larynx, lungs, and nasal cavity vary greatly in size and shape. , So the voiceprint patterns of any two people are different. This also makes voiceprint recognition a way of identity authentication. The so-called voiceprint recognition is to identify the identity through the sound wave spectrum that carries verbal information displayed by electro-acoustic instruments. Voiceprint recognition is very suitable for remote identity confirmation. It only needs a phone, mobile phone or microphone to realize remote login through the network. advantage Voiceprint extraction is convenient and can be done unknowingly, so the user's acceptance is also high. With remote identity confirmation, you only need a microphone, phone, or mobile phone to log in remotely through the network (communication network or Internet). The cost of acquiring voice recognition is low, and it is simple to use, just one microphone, and no additional recording equipment is needed when using communication equipment. The algorithm complexity of voiceprint recognition and confirmation is low. Disadvantage The voice of the same person is volatile and easily affected by physical conditions, age, emotions, and other external factors. One way of the vein recognition system is to obtain a personal vein distribution map through a vein recognition device, and extract feature values ​​from the vein distribution map according to a special comparison algorithm. Another way is to use an infrared CCD camera to obtain images of the veins of the fingers, palms, and back of the hand. The digital image is stored in the computer system to realize the feature value storage. During vein comparison, the vein map is taken in real time, the features are extracted from the digital image using advanced filtering, image binarization, and refinement methods, and the complex matching algorithm is used to compare and match the vein feature values ​​stored in the host, so as to perform individual matching. Identification, confirmation of identity. advantage It belongs to the characteristics of internal cattle, will not wear out, is more difficult to forge, and has high security. Vessel characteristics are usually more obvious, easy to identify, and good anti-interference. It can realize non-contact measurement, has good hygiene, and is easy for users to accept. Not easily affected by scratches or oil stains on the hand surface. Disadvantage The veins of the dorsal hand may still change with age and physiological changes, and the permanence has not been confirmed Although the possibility is small, there is still the possibility that the registration cannot be successfully registered. Because the collection method is limited by its own characteristics, it is difficult to miniaturize the product. The collection equipment has special requirements, the design is relatively complicated, and the manufacturing cost is high.
Whaylan 1500W portable solar power station.Large capacity, high endurance, a variety of ports, at any time for your need to charge the equipment. Completely say goodbye to the anxiety of outdoor electricity and devote yourself to an outdoor activity. At the same time, it can be equipped with solar panels to charge the power supply. The energy storage technology of lithium battery is combined with the clean renewable energy of solar energy to truly realize the enjoyment from day to night.
Whaylan is a member of USB-IF and WPC.Our factories are located in Dongguan and cover 10000 square meters, including about 400 1500W power station,powerstation 1500 watt,1500w portable power station suzhou whaylan new energy technology co., ltd , https://www.whaylan.com




well-trained workers,30 experienced engineers,35 QC employees, and 16 production lines. With the total capacity around 3 million pieces cables and power banks monthly.5-10 new designs will be launched each quarter to target updated market demand.