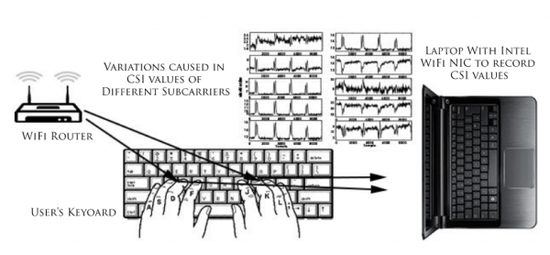
There is a secret security measure called "keystroke record", which forms password protection by recording the operator's keystroke habits. This is an upgrade method in security protection, but this type of biometrics is now also greatly hacked. According to foreign media reports, researchers from Michigan State University and Nanjing University in China have found a way to accurately detect keystroke records using a Wi-Fi signal through a common router. The researchers pointed out that in the minimal signal interference environment, the attacker can detect the user's hit record on the keyboard by interrupting the router WiFi signal, and then use the data to steal his password, the accuracy rate reached 77% to 97.5 %between. In addition to acquiring keystroke records, Wi-Fi signals can also be used to read user gestures and lip movements. In operation, in order to collect small changes in the WiFi signal, WiKey Lab researchers used the router's MIMO (Multiple Input Multiple Output) function to perform attack operations. With the help of collected WiFi signals and scanning of rooms, researchers can create an indoor environment map. When one is standing in front of a notebook and ready to input, WiKey can capture WiFi signal interference data caused by small changes in the user's hands, fingers, and keyboard. The researchers explained: “Every keystroke, the user will move his hands and fingers in a unique way and direction, then they will form a unique pattern in the time sequence of channel state information (CSI) values, we will call it The CSI waveform of this key." The research team stated that after acquiring the keystroke record data, the user's keystroke record can be converted into an input text record through a set of algorithms they developed. Researchers revealed that 77% to 97.5% accuracy rate allows attackers to know about three-quarters of the user's password. However, this method is also prone to bugs. When more than one laptop is placed in a room, it cannot determine the attack target. Non-Contact Detector,Non Contact Voltage Tester,Voltage Tester Pen,Non Contact Voltage Detector YINTE TOOLS (NINGBO) CO., LTD , https://www.yinte-tools.com