Network storage bandwidth optimization and protection In order to cover a wider market area and obtain higher profits, the growth of an enterprise is always directly represented by the growth of branches; at the same time, in order to achieve better business continuity, enterprises must also ensure daily business through means such as off-site data backup Smooth handling and recovery in a timely manner after a disaster. In the face of similar evolving application requirements, combining storage technology with the network is an inevitable choice in the industry: storage applications based on wide area networks (WAN) can greatly reduce the inconvenience caused by the spatial distance to the business, and achieve a wide range of connections and coverage . However, in practical applications, the deployment of network storage must also face and solve two key issues: bandwidth and security. There are always specific time requirements for the completion of storage applications (actually all applications), and network-based implementations are converted to network bandwidth requirements. To ensure the timely completion of related tasks, you must provide them with the necessary and sufficient network bandwidth On the other hand, the information (data) resources of an enterprise are directly related to its core competitiveness, and it is the most important asset of an enterprise. It should be properly protected under any conditions. Since the security of public networks cannot be guaranteed, enterprises often have to rent dedicated lines to deploy related network storage applications. With the continuous development of services, the gradually enriched applications have higher requirements on network bandwidth, and the expensive cost of leased private lines puts enterprises in a dilemma: not increasing the bandwidth of private lines will affect the development of the business; increasing the bandwidth of private lines The cost is too expensive and will consume a large amount of the company's new profits. In this case, the use of data compression-based network bandwidth optimization technology will greatly ease the pressure of data transmission. Based on the IPComp protocol architecture defined by RFC 3173, by compressing the IP message payload, a compression ratio of approximately 2: 1 is generally obtained (the compression ratio for a specific application is related to the compressed data). After using compression, the packet is reduced to half of the original, and accordingly, the demand for network bandwidth is reduced by 50%; when the network bandwidth is unchanged, it will be able to transmit twice the original data. In general network systems, data compression has very wide and mature applications. Major network equipment manufacturers represented by Cisco have provided support for data compression based on the LZS algorithm. On the other hand, because the price of leased leased lines is too expensive, using IPsec VPN based on the public Internet is a good alternative: IPsec VPN is directly based on a common public network and establishes a trusted connection between two sites through an encrypted tunnel. Compared with the dedicated line, access to IPsec VPN based on ordinary Internet will not increase additional network costs, the same expenditure will get much higher bandwidth. Moreover, IPsec VPN provides better flexibility. When the branch office is further increased, there is no need to re-add or deploy new network lines, and the reliable connection with the new branch office can be completed directly through the software policy configuration. However, due to the inherent security flaws of the public Internet, in order to provide reliable identity authentication, protect the integrity and confidentiality of data, and resist various possible hacker attacks, the construction of IPsec VPN introduces a very complete and complicated security protocol. And it needs complex encryption processing and encapsulation of the transmitted data. Traditional IPsec VPN deployments mostly rely on independent security gateways or IPsec VPN modules of specific network devices (routers, firewalls, etc.). In addition to additional equipment costs, the deployment, configuration, and maintenance of IPsec VPN are relatively complex, and are usually completed by professionals with the necessary security knowledge. Moreover, because security processing such as encryption requires a lot of CPU resources, high-performance IPsec VPN devices require the use of special security acceleration modules; at the same time, complex IPsec protocol processing often introduces large delays in the transmission of packets , May also cause some storage applications to fail to proceed or complete normally. To this end, as a long-term leader in the network security and storage optimization market, Hifn creatively proposed the FlowThrough security processing architecture, and based on mature chip technology, launched the Express DS4100 multi-function network card to provide a configuration for network storage manufacturers Simple, solution that can achieve both bandwidth optimization and IPsec VPN. Express DS4100 multi-function network card through integrated Hifn FlowThrough 8450 security processor and Intel 82576 network card chip, with standard small size (half height and half length) PCIe board provides dual Gigabit interface (optional fiber or RJ45 copper interface), can 4Gb / s line speed completes bandwidth optimization (compression) and protection (IPsec VPN), and can automatically manage network-based automatic key agreement (IKE), thereby simplifying bandwidth optimization and protection to a minimum of policy configuration, making complex The details of security and compression processing are transparent to the user. At the same time, with the excellent technical design, the delay introduced by the bandwidth optimization and protection processing of Express DS4100 is only about 4.5us, which will not bring any obstacle to the application. Only need to replace the ordinary Ethernet card with Express DS4100, the available bandwidth of the customer will be doubled, without adding any additional equipment or paying more line lease fees; at the same time, the simple IPsec VPN deployment will allow users to completely get rid of the lease Various restrictions on the line provide complete basic support for rapid business growth.
a thing that joins together two parts of sth, two vehicles or two pieces of equipment.
Custom Coupling,Coupling Of Encoders,Useful Coupling,Latest Coupling Yuheng Optics Co., Ltd.(Changchun) , https://www.yhencoder.com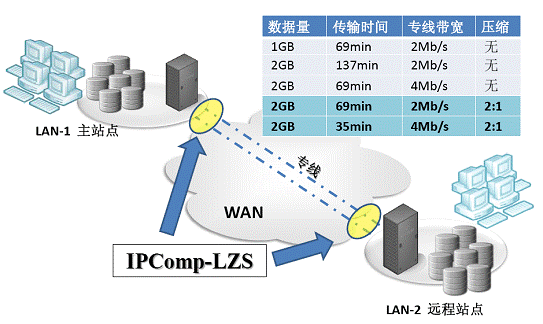
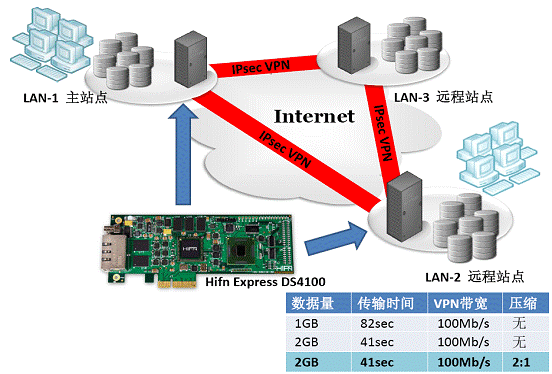
figure 2