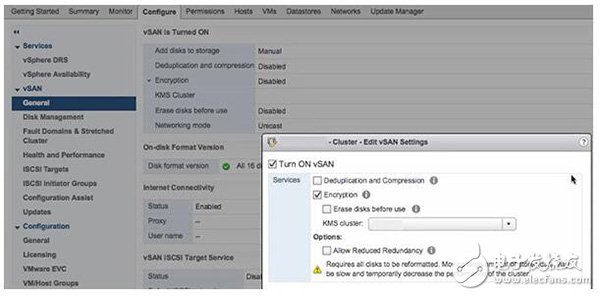
VMware vSAN 6.6 is the first software-defined storage product that includes hyper-convergence encryption within the hypervisor. vSAN 6.6 creates static data encryption in the vSAN kernel and is enabled cluster-wide, encrypting all objects in the vSAN data store. This new feature is called vSAN encryption. For most companies, network security is a top priority, so vSAN encryption is very popular. IT administrators have been unwilling to deploy encryption at the operating system level or allow application owners to encrypt applications and data. Static data encryption solves this problem by encrypting the data located on the vSAN data store. vSAN encryption has nothing to do with hardware, which means that administrators can choose the storage hardware devices they want without having to purchase expensive self-encrypting drivers. VSAN Encryption vs. vSphere Virtual Machine Encryption vSAN encryption can be used in mixed environments and all-flash configuration environments. A KMS compatible with Key Management Protocol 1.1 is required to communicate with vCenter Server. vSAN Encryption Use the xor-encrypt-xor-based tweaked-codebook mode to encrypt the caching layer and the storage layer using AES-256 XTS ciphers. vSAN encryption is also compatible with vSAN all-flash performance features such as deduplication, encryption, and erasure codes; this means that it delivers efficient, secure storage. It encrypts data as it enters the cache layer and decrypts it as it leaves the cache layer. Finally, data is deduplicated and compressed when it enters the storage tier, and it is encrypted again. The encryption mechanism of vSAN encryption is similar to that of vSphere 6.5 virtual machine encryption and uses the same encryption library provided by KMS. In fact, you can use the same KMS for vSAN encryption and virtual machine encryption. But there are no other similarities. Virtual machine encryption encrypts the virtual machine through the vSphere API for I/O filtering, while vSAN encryption encrypts the entire data store. The other major difference is that vSAN encryption uses Layer 2 encryption. It uses KEK encryption DEK. DEK is a randomly generated key that encrypts data on each disk. Each vSAN host stores the encrypted DEK but does not store the KEK on each disk. If the host needs KEK, it needs to apply to KMS. vSAN encryption works When vCenter Server requests AES-256 KEK from KMS, vSAN encryption comes into play. vCenter Server only stores the KEK ID and does not store the key. ESXi hosts use the industry-standard AES-256 XTS mode to encrypt disk data. Each disk has a unique, randomly generated DEK. Each ESXi host then uses KEK to encrypt the DEK and store the encrypted DEK on disk. The host does not store KEK on disk. If the host is restarted, the KEK is requested from the KMS using the corresponding ID. The host can decrypt the DEK on demand. The host uses the host key to encrypt the core dump instead of the data. All hosts in the same cluster use the same host key. VSAN encryption generates a random key to re-encrypt the core dump when collecting support bundles. Use a password when encrypting random keys. When the encrypted vSAN host is rebooted, the disk group is not mounted until it receives the KEK, which means the process may take several minutes. And the encryption process consumes CPU resources. AES-NI significantly improves cryptographic performance, so AES-NI is enabled in the system's basic input/output system. Encryption process To encrypt data using vSAN encryption, first add KMS to the vCenter Server and establish a trusted connection with it. Do not deploy KMS on datastores that attempt to encrypt because in the event of a failure, hosts in the vSAN cluster must communicate with the KMS. Select the vCenter Server where you want to deploy KMS. Under the Configuration tab, select Key Management Server and add KMS details. Figure 1 shows the options for establishing a trusted connection between vCenter, ESXi host, and KMS. Once one of the above options is selected, encryption can be enabled in the vSAN cluster. Figure 1. Choosing a digital certificate to establish trust with KMS Turning on vSAN encryption is very simple. Just select the vSAN cluster and enter the configuration tab. Under vSAN, select Generic. Click the Edit button and select the "Open vSAN", "Encryption" check box. Be sure to choose the right KMS cluster. Figure 2. Editing vSAN settings On this page, you should also see the "Clear disk before use" and "Reduce redundancy" options. The "Clear disk before use" option clears existing data on the storage device when it is encrypted. Be aware that this will increase disk formatting time. If the vSAN cluster has more virtual machines already deployed, and you realize that there is not enough free capacity for migrating data before encryption, the "reduce redundancy" option reduces the protection level of the virtual machine to free up the storage for performing encryption. space. This method does not migrate the data to other data in the cluster; just remove each disk group, upgrade the disk format, and then add the disk group back. All objects are still available but reduced redundancy. Once you click OK, vSAN will reformat all disks in the disk group. Each time vSAN removes a disk group, it transfers the data in the disk group, formats each disk in the on-disk 5.0 format, recreates the disk group and continues processing the next disk group. This can take considerable time, especially if vSAN needs to migrate large amounts of data during reformatting. Note that if you choose to disable vSAN encryption at any point in time, vSAN will perform a similar reformatting process to remove disk encryption. If you need to regenerate the encryption key, you can do it in the vSAN configuration user interface. There are two ways to regenerate the key. The first is to use the new KEK to encrypt the existing DEK. Another way is to completely re-encrypt all data using KEK and DEK. The latter method takes a long time because all data must be re-encrypted with the new key. To generate a new encryption key, click the Configuration tab. Under vSAN, select Generic and click Generate New Encryption Key. This will open a window where you can generate a new encryption key and re-encrypt all data in the vSAN cluster. To generate a brand new KEK, click OK. DEK will use the new DEY re-encryption. To generate a brand-new KEK and a brand-new DEK and re-encrypt all data in the vSAN cluster, you need to select the checkbox "Also use the new key to re-encrypt all data on the storage." VOZOL BAR 2200 Vape are so convenient, portable, and small volume, you just need to take them vozol bar 2200 disposable vape,vozol bar 2200 vape kit,vozol bar 2200 puffs vape,vozol bar 2200 vape pen,vozol bar 2200 e-cigarette Ningbo Autrends International Trade Co.,Ltd. , https://www.ecigarettevapepods.com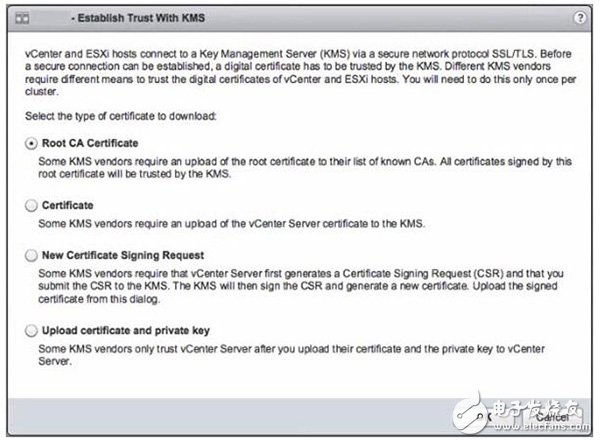
out of your pocket and take a puff, feel the cloud of smoke, and the fragrance of fruit surrounding you. It's so great.
We are China leading manufacturer and supplier of Disposable Vapes puff bars, vozol bar 2200 disposable vape,
vozol bar 2200 vape kit,vozol bar 2200 puffs vape, and e-cigarette kit, and we specialize in disposable vapes,
e-cigarette vape pens, e-cigarette kits, etc.